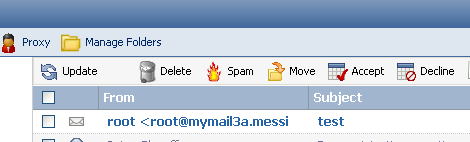
This hack implements a "Spam" button in GroupWise WebAccess. The "Spam" button appears next to the Delete button. Clicking it will feed the message back to the spam filter as a false negative, so the spam filter can learn from its mistake. The selected message is then moved to the Junk Mail folder.
Basically, you need to tell your users to click "Spam" to get rid of a message that's spam.
Here's a screenshot showing the new "Spam" button, with its icon, in the WebAccess toolbar.

At Messiah College, we use GroupWise for our email, in conjunction with SpamAssassin to filter incoming email. We have enabled the use of Bayesian classification in SpamAssassin to improve message filtering. Bayesian classification works best when you can give it feedback. Feedback consisted of taking a message that was classified incorrectly, and forwarding it, as an attachment, back to the spam filter. This was hard to use, but those that took the effort to do this reported a remarkable increase in the spam filter's accuracy.
The goal of this hack is to make the process of feeding a message back to the spam filter as easy as possible. This is achieved by adding a new button, labeled "Spam", to the WebAccess interface. The button is placed next to the "Delete" button; it's an alternative way to dispose of a message.
When "Spam" is clicked, the message is removed from the Inbox, with the added benefit that the spam filter is notified that the message was spam. This way, future messages from the same source, or with similar content, can be classified as spam.
The hack consists of some modifications to the WebAccess templates, an Apache rewrite rule that can intercept when the "Spam" button is clicked, and a CGI script to handle downloading the message and feeding it to the spam filter.
When the CGI script is invoked, it receives an HTTP request directly from the client. It copies the WebAccess session identifier and security cookie from that request and uses these parameters to send its own request to WebAccess, in order to download the raw content of the message being reported. It takes this raw content and *emails* it to the preconfigured spam-filter-feedback address. Next, the CGI script constructs a new URL to give to the client. This new URL will have WebAccess move the selected message(s) to the Junk Mail folder.
The hack is written again particular versions of GroupWise. Depending on which version of GroupWise you have on your system, you can download one of the following versions:
| GroupWise Version | Download |
|---|---|
| 8.0.0HP2 | spambtn-0.2.zip |
| 7.0.2 | spambtn-0.1.zip |
If you are running a version of GroupWise not listed above, pick the closest matching version and see how far you get. If you have a nearly matching version, but the fix does not apply cleanly, contact me and I may be able to help you out (for a consulting fee).
This hack makes the following assumptions:
* SuSE Linux Enterprise Server 10
* Apache2 and Tomcat5
* with GroupWise 8:
* WebAccess agent
* WebAccess application
1. Configure WebAccess application:
* Uncheck Use client IP in securing sessions
2. Install these Perl modules (from CPAN)
* LWP::UserAgent
FYI- to install a CPAN module, run (as root)
perl -MCPAN -e 'install "MODULE"'
where MODULE is the name of the module to install
3. Copy the following files to /srv/www/cgi-bin:
* learnspam.cgi
(Make sure that learnspam.cgi has "execute" permissions.)
4. Customize the parameters in learnspam.cgi to suit your needs.
5. If Tomcat hasn't been started yet, start it now, with
/etc/init.d/tomcat5 start
After it is started, you should see files extracted in
/srv/www/tomcat5/base/webapps/gw
For the following steps use that path in place of $gwdir.
6. Copy the following files into $gwdir/webaccess/200905172308/images:
* act_spam.png
* act_unspam.png
7. Copy the following files into $gwdir/WEB-INF/classes/templates/webacc/css:
* delete-as-spam-button.inc
* delete-as-spam-msglist-button.inc
* spambtn_fldrlist.htt
8. Apply the webaccess-templates-gw8.patch file to $gwdir...
cd $gwdir
patch -p1 < /path/to/webaccess-templates-gw8.patch
9. Edit /etc/sysconfig/apache2:
look for, and add if it is missing, these two modules in the
APACHE_MODULES list:
cgi
rewrite
10. Edit /etc/apache2/vhosts.d/vhost.conf. Insert the
following before the first directive.
RewriteEngine On
# LEARN actions get processed by a Perl script
RewriteCond %{QUERY_STRING} action=LEARN
RewriteRule ^/gw/webacc$ /cgi-bin/learn_spam.cgi [L,PT]
11. Edit /etc/apache2/vhosts.d/vhost-ssl.conf. Repeat the same
edit as for vhost.conf.
12. /etc/init.d/tomcat5 restart && /etc/init.d/apache2 reload
Send me feedback! Email jlong@messiah.edu.
Last updated: 2009-07-30